The Ultimate Guide to Federal Risk and Authorization Management Program (FedRAMP)
CYBERSECURITY
/
January 28, 2026

Welcome to the ultimate reference for the Federal Risk and Authorization Management Program. Many technology professionals ask what is FedRAMP and why it matters. In simple terms, it is a government-wide program that sets consistent requirements for cloud products and services used by public sector entities. The FedRAMP meaning points to uniform rules, enhanced data protection, and greater trust in cloud environments. It helps federal offices feel confident when they choose modern cloud solutions, since protection of sensitive data remains a top priority. The program provides a repeatable structure that cloud vendors must follow, which reduces risk and saves time for all parties involved. In this guide, we cover the essentials of compliance, certification, expected timelines, and effective best practices. We also highlight how cloud service providers can gain a competitive edge in a demanding marketplace. Let’s begin this journey toward a deeper understanding of this important government initiative.
FedRAMP Overview
The FedRAMP program offers a unified method for cloud security across public sector organizations. It was created to reduce complexity when multiple agencies need safe cloud solutions. This system outlines baseline measures to control potential threats. Its objective involves lowering the barriers that block federal institutions from embracing new technologies.
Many wonder what is FedRAMP compliance and why it matters. At its core, it is a pathway that helps a vendor prove its commitment to safeguarding information in hosted environments. When a company follows these guidelines, it shows it meets a list of standards designed to protect data. This leads to more trust across the federal government, since agencies can see consistent security levels.
The official name, or federal risk and authorization approach, revolves around identifying issues and verifying them through a structured lifecycle. That structure was built to simplify risk and authorization management. The baseline includes documentation, testing, and ongoing checks. It is sometimes called the authorization management program FedRAMP because it manages how providers handle security tasks. Details can get complex, yet the program’s mission is to make sure any solution working with government data meets approved requirements.
This FedRAMP overview is an entry point into the entire process. The program sets a common language for data protection by bundling policies, procedures, and control sets. That framework lets agencies compare vendors on the same scale. It saves time and resources, because leaders do not need to reinvent the wheel whenever they analyze new cloud services.
Every year, more organizations pursue FedRAMP compliance to expand opportunities and meet federal needs. Agencies look for validated solutions that can handle sensitive workloads in a consistent manner. By unifying these expectations, the program reduces guesswork and fosters trust across the public sector. It also encourages continuous modernization within service environments.
Through this guided approach, each provider has a clear set of standards. These standards strengthen data management in a landscape filled with emerging digital threats, making it easier to protect essential information assets.
Key FedRAMP Requirements
Each vendor seeking acceptance must address certain FedRAMP requirements that shape the path to secure operations. These conditions include robust data encryption, strict access control, and detailed logging of user activities. They also involve continuous checks that verify ongoing compliance with baseline controls. When organizations align with these expectations, they become FedRAMP compliant, a status that signals readiness to protect sensitive federal information.
Clear FedRAMP standards exist to bring uniformity across multiple environments. These standards define the types of controls providers should apply at various impact levels: low, moderate, or high. Vendors that fall under the moderate or high categories face heavier scrutiny, due to the potential consequences for national interests. Security parameters cover everything from identity management to incident response strategies.
The program classifies cloud services into three impact levels, Low, Moderate, and High, based on the potential harm that could result from a security breach. Each level dictates the number and rigor of the security controls a provider must implement, ensuring that protection is proportional to the data's sensitivity.[1]
Among all FedRAMP compliance requirements, there is a strong focus on formal documentation. This includes policies, procedures, and test plans. That paperwork creates transparency, which government reviewers rely on when determining risk levels. Many government agencies count on the program’s structured approach to reduce the burden of evaluating each vendor independently. Clear instructions for risk evaluation remove guesswork and help decision-makers pinpoint solutions that match mission goals.
Defined FedRAMP guidelines outline steps that each cloud service must fulfill. These guidelines detail how data is handled, who can access it, and how incidents are reported. Providers also perform thorough cloud security checks to confirm that protective measures are in place. This helps unify security protocols across an otherwise diverse federal ecosystem.
When an organization meets these core conditions, it gains trust in the eyes of procurement officers who manage technology decisions for federal offices. That leads to new opportunities, since agencies prefer proven solutions that fulfill regulatory standards. Attaining compliance means meeting the hallmark features of an established system, which streamlines the entire adoption cycle.
Another key element involves consistent monitoring of vulnerabilities and mitigation steps. The program expects each provider to carry out regular testing and reporting, ensuring that all controls remain effective. Such an organized structure simplifies risk management and keeps pace with rapid digital innovations.
The FedRAMP Process
The official steps, often called the FedRAMP process, lay out how a vendor demonstrates readiness and meets uniform benchmarks. This journey begins with a thorough review of system documentation. That includes everything from operational procedures to incident response plans. A formal security assessment follows, carried out by an independent group that examines controls and tests for possible gaps.
This step-by-step method is integral to FedRAMP cloud security, since it provides assurance that key measures are in place. The sequence usually starts with providers preparing a detailed package of policies. Then a security and risk assessment checks the alignment of those policies with government protocols. This evaluation covers data confidentiality, integrity, and availability at different impact levels. Once the assessment is complete, the results feed into a final report that shows whether the system meets the baseline set by the program.
As part of the FedRAMP compliance process, providers address any shortcomings found during the evaluation. That might involve improving identity management, enhancing encryption layers, or adjusting event monitoring strategies. Once corrections are made, a final review determines the outcome. If everything meets the required level, the solution is deemed fit for cloud services in the public sector.
Security controls remain at the heart of these steps. They define the protective measures a system needs, such as access restrictions, encryption standards, and vulnerability scanning. These controls align with broader federal best practices and reflect industry norms. Each environment’s threat profile dictates the level of scrutiny needed. Systems with sensitive workloads typically undergo deeper testing and require more robust controls.
The foundation of the FedRAMP program is built upon the security and privacy controls outlined in NIST Special Publication (SP) 800-53. FedRAMP adapts this comprehensive catalog of controls to the specific needs of cloud environments, ensuring a consistent and robust security baseline that aligns with federal information systems.[2]
By following the FedRAMP process, an organization demonstrates a strong commitment to safeguarding public sector data. That commitment fosters trust among procurement teams and promotes deeper collaboration across agencies that rely on secure digital infrastructure. Over time, consistent adherence leads to an advanced security posture that benefits providers and end users alike.
Understanding What is FedRAMP Certification
Many service providers ask what is FedRAMP certification and why it holds value. This approval is a formal recognition that a cloud solution has passed strict reviews and meets the core requirements of the program. It proves that the system can protect federal data in a reliable way. Achieving this status also opens the door to new opportunities, since public sector organizations often need a solution that satisfies these benchmarks.
The FedRAMP certification process involves multiple stages. First, a provider prepares detailed documentation that explains how its environment meets each security control. Next, an authorized assessor inspects every element of the setup. That includes network architecture, access protocols, and incident response measures. These inspections lead to a final report, which an oversight body examines before granting approval. This path offers a standardized way to gauge compliance across different providers and remove guesswork for agencies that want to adopt cloud-based tools.
Questions around how to get FedRAMP certified often center on the time and resources required. A vendor must align its technical environment with the baseline set by the program, including encryption, logging, and strong identity management. The timeline can vary, but it often includes thorough planning, technical updates, and repeated testing. That journey can feel lengthy, yet it gives a powerful advantage once done.
Meeting FedRAMP certification requirements is not only about passing a single test. It requires ongoing efforts to keep performance stable in real-world conditions. Factors like new vulnerabilities, system upgrades, and shifting government priorities may prompt reevaluation. This is where continuous oversight matters. Maintaining compliant status demands constant focus on every aspect of security.
Once a provider is FedRAMP certified, it gains a competitive edge in the marketplace and becomes a trusted partner for public sector initiatives. Finally, FedRAMP accreditation signals that the provider has reached the quality bar set by federal stakeholders. This label demonstrates a firm commitment to protecting government data, which boosts credibility and fosters trust with agency clients.
Timelines and Authorization
Many organizations ask how long does it take to get FedRAMP certified. There is no single answer, since each system has unique complexities that can affect the overall pace. Some providers require a few months to align with the guidelines, while others may need a year or more. It depends on factors like existing security measures, internal resources, and the specific impact level.
The FedRAMP authorization process has a few distinct paths, including one led by the joint authorization board and another driven by individual agencies. The board, sometimes called the JAB, includes chief information officers from key federal entities. The board route can lead to a JAB provisional authority, which multiple agencies may then leverage. A different route is the agency authorization path, where a single federal agency takes the lead in reviewing a solution. Either way, the end goal is to achieve FedRAMP authorization that reflects official approval from top stakeholders.
FedRAMP offers two primary paths for authorization: the Joint Authorization Board (JAB) Provisional Authority to Operate (P-ATO) and the Agency Authorization. JAB authorization is leveraged by multiple federal agencies and is issued by representatives from the Department of Defense, Department of Homeland Security, and the General Services Administration. An Agency Authorization is a more common path where a single federal agency sponsors a cloud service for its own use. [1]
When organizations ask when is FedRAMP required, the short reply is that any cloud offering that handles government information often needs this clearance. Each federal agencies has some flexibility in choosing its technology stack, yet solutions that store or process sensitive data usually must meet these rules. This applies across many sectors, from defense to civilian offices.
To achieve authorization, a provider follows a defined authorization process that validates security controls, incident response capabilities, and other vital elements. Once all checks are complete, final sign-off grants permission to operate in public sector environments. That status applies across multiple federal government agencies, allowing them to use the same service without repeating the entire review. It is a model that saves effort and encourages cooperation among diverse government units.
Vendors that fulfill every step find that the journey can unlock broader relationships and long-term partnerships in the public domain.
Achieving FedRAMP Authorization
Gaining official FedRAMP authorization begins with a structured plan. That plan includes a system security plan outlining how each control is met, an organizational chart of responsibilities, and a risk management strategy. This documentation sets the stage for a detailed review later in the cycle.
A full security assessment follows, carried out by a third-party assessment organization. Their role is to perform FedRAMP assessments that confirm the provider’s controls align with the FedRAMP framework. The process often starts with a readiness assessment, checking if the provider has adequate foundational elements in place. This can lead to a readiness assessment report highlighting any gaps. Providers usually fix these issues before moving forward with the official evaluation.
During the formal assessment, the external team compiles a security assessment report that details each control tested, any vulnerabilities found, and how the provider plans to address them. Once the assessment is complete, the results go to federal reviewers who decide if the solution meets the required FedRAMP cloud requirements. The provider may receive requests for clarification or extra tests to address open questions.
If reviewers approve the final package, the solution obtains FedRAMP authorization status. From that point, it gains an official listing that public sector groups can adopt. This removes the need for each agency to run a separate, full-scale check. The centralized model speeds up the vetting process, saving time across the public sector.
That unified approach not only ensures compliance but also builds confidence in shared solutions. By following a single set of standards, providers can reach multiple agencies simultaneously. In a setting where time and resources count, efficiency can be a significant advantage for vendors pursuing wider public sector engagement. Staying on track with routine monitoring and regular checks remains a core part of sustaining this authorization over the long term.
Following a security authorization, FedRAMP mandates continuous monitoring, a core tenet of the NIST framework. Providers must regularly conduct vulnerability scans, penetration testing, and submit continuous monitoring reports to the authorizing body. This ongoing effort ensures that the security posture of the cloud service remains effective against evolving threats.[1]
Figure. 1: Security Domain Implementation Metrics
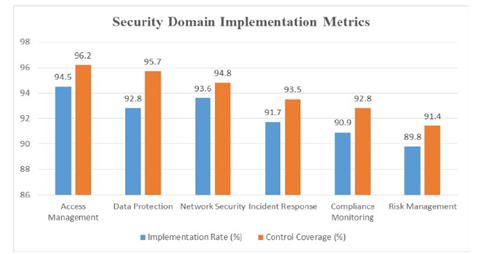
The continuous nature of FedRAMP compliance requires providers to track performance using detailed metrics. As illustrated by the Security Domain Implementation Metrics, success is measured not only by the actual rate of control deployment (Implementation Rate) but also by ensuring all necessary security controls are included within the system's authorization boundary (Control Coverage). This data shows that areas critical to FedRAMP, such as Access Management and Data Protection, achieve high coverage, while process-dependent domains like Risk Management often require focused and continuous effort to close the gap between desired coverage and actual implementation [3].
Best Practices for FedRAMP Cloud Security
Maintaining strong protection is an ongoing endeavor. Many providers focus on continuous monitoring to spot new risks. That involves regular scans for weaknesses, real-time alerts, and prompt patch management. Frequent penetration testing also helps detect flaws before they become critical threats. By simulating attacks, teams learn how the system responds and take early steps to strengthen defenses.
Central to FedRAMP security controls is the notion that protection must adapt over time. As threats evolve, organizations update their measures to remain effective. This may mean introducing new identity checks or dividing the network into smaller segments to contain problems if they happen. The overall aim is to keep data secure in the face of shifting risks.
Collaboration with agencies like the department of homeland security can add extra insight. By sharing data about emerging cyber threats, both sides gain deeper awareness of potential vulnerabilities. It also creates stronger bonds between public and private groups. That shared knowledge leads to better readiness and a common view of security challenges.
Providers also refine incident response plans to align with the guidelines. That involves defined procedures to identify, analyze, and contain any breach. Prompt reporting is essential to maintaining trust, which underpins the entire program. If a vendor proves it can handle surprises in a steady way, it builds a reputation as a reliable partner.
Industry leaders treat compliance as more than a box to check. They invest in encryption, detailed logging, and training for users to improve awareness. These measures create a culture where protection is part of daily life. That mindset keeps each provider prepared for new challenges and helps ensure that sensitive government information remains safe.
Fig. 2: Cloud Security Implementation and Improvement Matrix
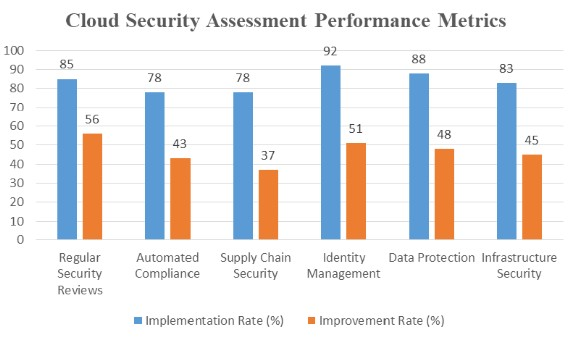
Building a FedRAMP Program
Launching a comprehensive plan involves cooperation across various teams. The FedRAMP program management office is a central resource for guidance and announcements. It interprets requirements, sets milestones, and coordinates with relevant authorities. Larger vendors may set up their own program management office to unite every step, from security tasks to communication with stakeholders.
An organization that wants to thrive in this domain defines itself as a cloud service provider with suitable expertise. It may present cloud service offerings that cater to specialized or broad-based needs, such as analytics or communication tools. A single cloud service offering might solve a niche problem, while an extensive range covers many tasks. Either way, the goal is to deliver secure cloud services that handle federal workloads without compromising confidentiality.
The general services administration maintains official listings of authorized cloud products. This mechanism helps agencies locate solutions that hold a FedRAMP designation or are in the process of acquiring it. Such listings streamline the adoption of secure cloud by letting agencies pick from pre-approved options. Vendors with these recognitions gain higher visibility and can showcase their capabilities to a wide range of government clients.
A key resource for both vendors and agencies is the FedRAMP Marketplace. This public database lists all cloud services that have achieved authorization or are in the process of doing so. It streamlines the procurement process for government agencies by providing a central hub of pre-vetted, compliant solutions, boosting visibility for authorized providers.[1]
Reaching an advanced standing usually involves continuous improvement. Even after passing initial checks, a solution may face new demands when technology shifts. Teams overseeing these systems watch for changes in policy or potential threats. Many providers also run ongoing training to keep staff aware of new methods and responsibilities. That diligence helps the solution remain both compliant and up to date.
Real success arises when organizations balance security with innovation. By blending strict protective measures, user-friendly design, and responsive support, providers can build lasting relationships with government buyers. In the end, a well-executed program approach paves the way for steady expansion and ongoing trust in vital public sector operations.
Conclusion
FedRAMP stands out as a unifying model for cloud-based solutions in the public sector. It defines a shared standard for protecting information, handling incidents, and sustaining secure operations. Organizations that follow these requirements lower risks and strengthen partnerships. Over time, compliance leads to fresh opportunities that benefit both vendors and government bodies. This guide covered each core step, from initial planning to full authorization. Proper understanding of these elements helps any team anticipate challenges and craft sustainable strategies. In essence, the program foster’s reliability and confidence in an ever-changing digital environment.
Ready to explore a secure future with government clients?
CyberCrest can help you navigate the path to becoming FedRAMP compliant. Our specialized support includes gap analyses, readiness preparations, and complete assessments. We stand by your side at each stage to confirm that your controls meet every expectation. If you aim to grow in the public sector, let our experts be your trusted guides. Contact us now to discover how we can simplify your compliance approach and minimize uncertainties. Achieve new levels of success, open doors to valuable contracts, and show your dedication to protecting critical data. Get in touch and begin your journey.
{{cta}}
References:
- FedRAMP.gov. https://www.fedramp.gov/
- NIST Special Publication 800-53, Revision 5. https://csrc.nist.gov/pubs/sp/800/53/r5/upd1/final
- Kopparthi, V. J. R. (2024). Federal Cloud Security: A Strategic Approach to FedRAMP Compliance and Governance. DOI:10.5281/zenodo.14500455.Available: https://www.researchgate.net/publication/387276886_Federal_Cloud_Security_A_Strategic_Approach_to_FedRAMP_Compliance_and_Governance


FAQ
What is the simplest FedRAMP definition?
It is a government-led approach for making sure cloud services meet strict security rules. It creates a single framework that unifies multiple agencies and providers under one consistent standard.
Do all providers need to comply?
Many organizations ask if they must complete this process. Public sector solutions typically need it, especially if they handle sensitive data or involve higher impact levels.
How does FedRAMP differ from other frameworks?
It centralizes security reviews for government customers. Once a provider secures authorization, several agencies can adopt it without repeating the entire review.
Does it replace other certifications or audits?
Not always. Certain providers also hold credentials like ISO 27001 or SOC 2. FedRAMP focuses on federal needs, which can be stricter in some areas.
How often are updates or renewals required?
The program expects constant upkeep through monitoring and periodic re-checks. That way, controls stay effective as threats and technology evolve.
Where can an organization get official guidance?
The program’s website has step-by-step resources. Many consultancies also offer help to interpret guidelines and close any gaps.
Can existing solutions become authorized?
Yes. Most providers can adapt their existing platforms to meet the baseline. This could involve stronger encryption, better incident responses, or new documentation. Careful planning and thorough testing accelerate this transition and promote lasting compliance.





















